In today’s world, where data is as valuable as gold, safeguarding intellectual property is crucial. This is particularly true in high-stakes sectors like biotechnology. With this in mind, a top biotechnology firm joined forces with dig8ital. Together, we embarked on a strategic project to strengthen the company’s security architecture.
Our main aim was to protect the firm’s most valuable asset: its intellectual property. This includes unique research data, patented processes, and confidential partnerships. Given the sensitive nature of these assets, we planned the project carefully and executed it in stages. Each stage built on the last, creating a comprehensive cybersecurity strategy. This approach not only met immediate needs but also offered a scalable solution for the future.
In this article, we’ll guide you through our journey. We’ll detail how we got to know the business, set its objectives, and translated these into robust security measures. The outcome is a cutting-edge security architecture. It not only safeguards the firm’s critical assets but also sets the stage for sustainable growth in a competitive market.
For a more in-depth understanding of security architecture and its critical components, don’t miss this essential read: What is Security Architecture, and What Do You Need to Know?.
Understanding the business: A deep dive into objectives and requirements
The first and perhaps the most crucial phase of the project was dedicated to understanding the business in its entirety. Given that the biotechnology sector is complex and highly specialized, it was imperative to gain insights directly from the key stakeholders within the organization. This would ensure that the security architecture we were about to design would be closely aligned with the company’s core objectives and operational needs.
Stakeholder interviews
To initiate this phase, our team at dig8ital scheduled a series of detailed interviews with key figures from diverse departments such as Research & Development, Operations, Legal & Compliance, and IT. Our goal was to pinpoint the main business objectives for each department and to grasp the unique challenges they encountered in meeting these objectives.
For example, the R&D team prioritized the safeguarding of unique research data and the establishment of secure channels for collaborating with external research partners. Meanwhile, the Operations team stressed the importance of maintaining seamless workflow systems for daily business activities.
Identifying business objectives and requirements
In our interviews, we pinpointed three key business objectives that stood out:
- Intellectual Property Protection: Safeguarding proprietary research and patented methods emerged as the top priority.
- Streamlined Operations: The focus here was on optimizing both technological and procedural workflows to maximize productivity while minimizing disruptions.
- Compliance with Regulations: Upholding strict compliance with industry rules and legal mandates was crucial for preserving the company’s reputation and market position.
Mapping out business requirements
After defining the objectives clearly, we moved on to pinpoint the business requirements that would support these goals. These requirements mainly consisted of specific processes and technologies crucial to the organization.
For instance, the R&D team heavily depended on a specialized system for data management to store research findings. In contrast, the Operations team had an intricate supply chain framework in place.
Equally vital was understanding the technology landscape. We charted the existing IT infrastructure, which included legacy systems, databases, and services from third parties. This gave us a complete view of the technological dependencies. In the same vein, we recorded essential operational processes like methods for collecting data, approving workflows, and protocols for emergency response. This insight allowed us to grasp the intricate relationship between technology and processes in meeting the company’s business objectives.
By the end of this phase, we gained a thorough understanding of the organization’s business objectives and the essential requirements—both technological and procedural—to achieve them. This foundational insight would guide the next phases of the project, ensuring the security measures we put in place would be both effective and in alignment with the company’s primary objectives.
Translating Business into Security Requirements: Bridging the Gap with a Control Framework
After fully understanding the business objectives and their corresponding requirements, we moved on to the crucial task of converting these into actionable security requirements. Our goal was to match each business requirement with a set of security measures. This would protect the organization’s objectives without sacrificing efficiency or compliance.
Defining Security Requirements for Each Business Requirement
For each business requirement we pinpointed, we drafted a set of overarching security requirements. For example, to protect intellectual property, we needed secure data storage and limited access to sensitive information. To maintain operational efficiency, we focused on ensuring the integrity and availability of key systems. To meet regulatory compliance, we included requirements for data protection and audit trails.
Leveraging Artificial Intelligence for Control Framework
To put these security requirements into action, we used advanced AI tools. These helped us create a strong set of controls for each requirement. These controls made up our Control Framework, a detailed guide for implementing security measures throughout the organization. A unique feature of our Control Framework was its alignment with well-known cybersecurity standards like NIST and ISO27001. By linking our controls to these established frameworks, we made sure our approach was both thorough and in line with globally accepted best practices. This will make future audits and compliance checks easier, adding another layer of trust to our security architecture.
For an in-depth look at the security frameworks we use to map our own Security Control Frameworks, visit the official pages of two industry standards: ISO27001 Security Framework and NIST Cybersecurity Framework.
The Final Control Framework
The final product was a dynamic Control Framework. It was custom-fit to the organization’s unique needs but also adaptable to change. The framework included a broad array of controls, from managing access and encrypting data to responding to incidents and auditing for compliance. Each control linked to one or more security requirements, which were in turn tied to key business objectives.
This detailed alignment ensured that the organization’s security measures were not just strong but also closely connected to its business goals. This became crucial in later project phases, especially during gap analysis and risk assessment. It offered a clear roadmap for prioritizing and rolling out security measures.
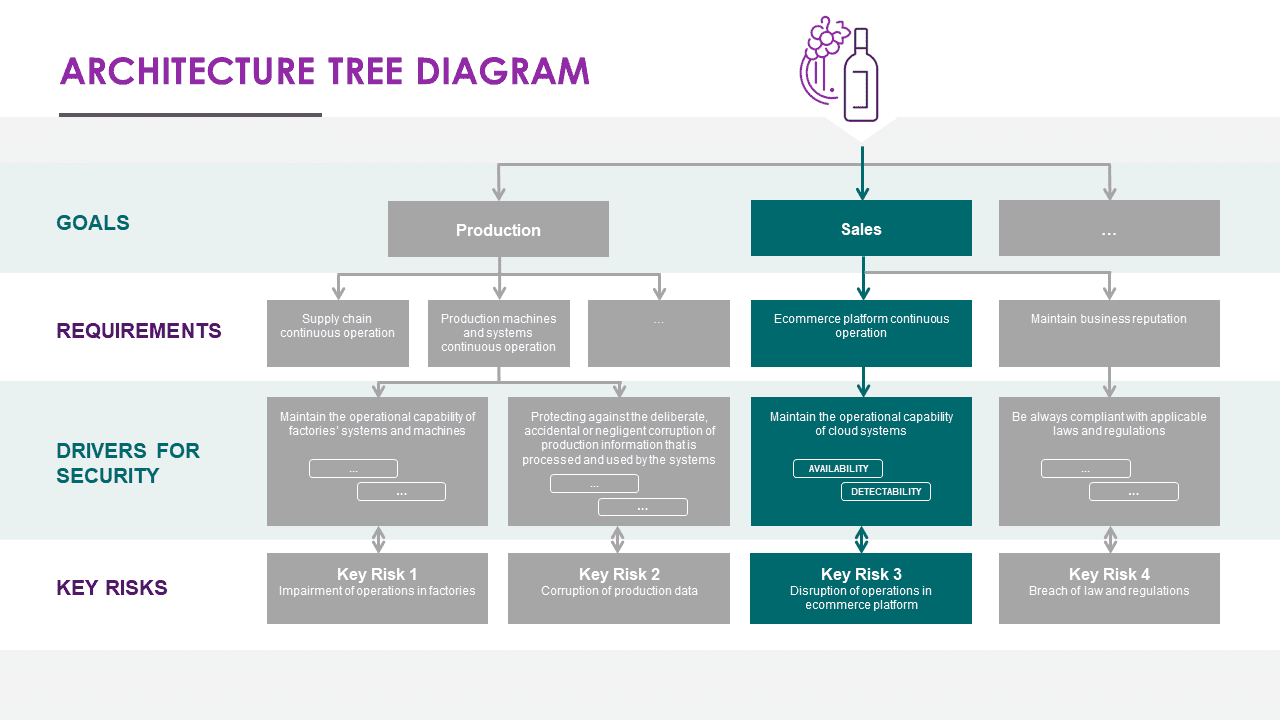
Example: Architecture Diagram for a Winery
To provide a concrete example of how the architecture diagram would look, let’s consider a simplified case for a winery. The diagram would visually represent the different layers of the architecture, starting from business objectives down to security controls and main risks.
Gap Analysis and Risk Assessment
Gap Analysis
The subsequent phase in our security strategy involved conducting a Gap Analysis. This analysis was centered on the Control Framework we had established. This targeted approach allowed us to focus our resources on the most critical business areas. It helped us avoid the common mistake of trying to secure everything, thereby diluting our efforts.
Risk Assessment
After identifying the gaps, we moved on to converting these security shortcomings into business risks. This phase is vital because it enables us to communicate in terms that the business understands, making it easier for stakeholders to grasp the consequences of not filling these gaps.
To aid in this process, we created a Key Risk Calculator. This specialized tool evaluates the likelihood and impact of each gap on the company’s objectives. By entering different factors, such as the type of gap, the sensitivity of the involved data, and potential financial or reputational repercussions, the calculator offers a measurable risk assessment.
For those interested in diving deeper into risk analysis and building a risk calculator, check out this Comprehensive Guide to Risk Analysis and Building a Risk Calculator.
This risk score is then mapped to the business objectives, providing a clear picture of how each security gap could affect the organization’s goals. This makes it easier to prioritize remediation efforts and allocate resources more effectively.
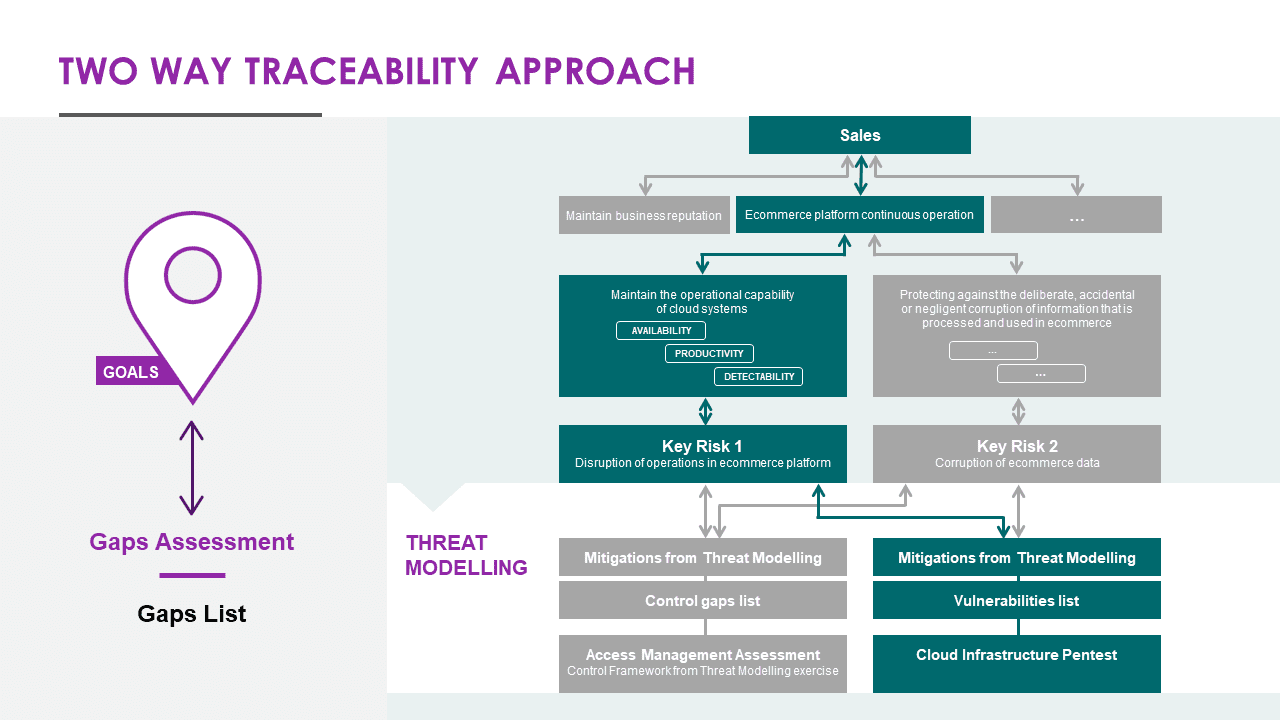
Example of Traceability: From Business Objectives to Security Gaps
In the accompanying diagram, you’ll see a multi-layered architecture that captures our method for aligning cybersecurity with business goals. Arrows in the diagram show the flow from business objectives to security controls and back, highlighting the traceability and alignment between business and security efforts.
Conclusion
The project effectively set up a strong security framework that safeguards the company’s intellectual property and aligns seamlessly with its business goals. This two-way traceability between business and cybersecurity ensures that security measures will adapt as the business evolves, offering a sustainable and secure operational setting.
By adopting a comprehensive approach that began with grasping business objectives and ended with the rollout of customized security controls, the company has notably lowered its risk profile. At the same time, it stays agile and competitive in the rapidly changing biotechnology landscape.
Interested in learning more about our unique approach to aligning business and cybersecurity? Feel free to reach out. We’re here to help you implement a robust security architecture that not only protects your assets but also supports your business objectives. Let’s work together to make your company more secure and competitive. Contact us today!