TECHNICAL SECURITY
INCREASE VISIBILITY AND STRENGTHEN YOUR CYBER RESILIENCE
Cyber security is not a set and forget initiative, nor can it be fully automated. While automated tools do help, any company looking to prepare itself against future attacks must have the backing of real, professional cyber security experts.
At dig8ital, our certified consultants can help build your cyber resilience with tried and true security assessments, tests and services, tailored to suit your unique requirements.
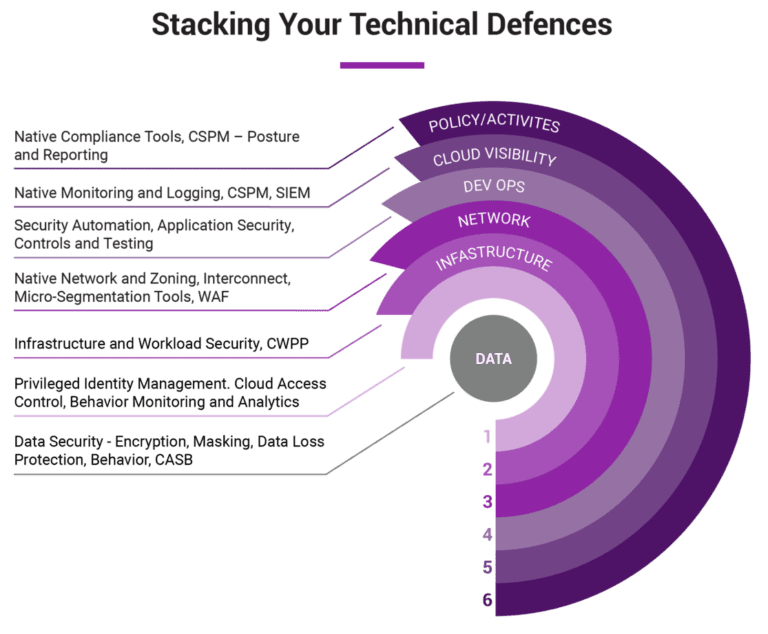
HOW CAN DIG8ITAL HELP?
- Cyber Resilience Strengthening
- Security Information and Event Management (SIEM)
- Security Testing
- Identity and Access Management (IAM)
- Vulnerability Management
- Security Operations
STRENGTHENING YOUR CYBER RESILIENCE
We utilize a range of products and services to strengthen an organization’s cyber resilience and give it complete visibility across
its digital platforms.
These include:
- Identity and Access Management
- Secure Collaboration
- Threat Detection
- Network, Application and Database Firewall technologies
- Data Encryption
- Anti MalwareData Loss Prevention
- Real World Security Training
- Real-time Threat Detection
- Cloud Access Security Brokers
- Breach and Attack Simulation
- Application and Code Security Analysis
- Network Visibility
- Secure Storage Solutions
At dig8ital, our consultants are CREST and OSCP-certified to carry out modern security testing procedures. Our
methods include:
- Continuous Security Integration (CSI)
- Shift Left Testing
- Dashboards
- Penetration Testing
- Vulnerability Assessments
- Dynamic Code Analysis
- Static Code Analysis
- Implementation of Secure Systems Development Lifecycle processes (SSDLC)
SECURITY TESTING
It takes a range of methodologies to properly test a company’s cyber security defence. It must be pushed to its limits, where its weak points become clear.
In order to better ensure your company is ready for a wide range of potential attacks, you need comprehensive security testing in a variety of formats, such as ethical hacking, using a combination of recognized methods and standards.

VULNERABILITY MANAGEMENT
It’s almost impossible for security teams to keep up with the expansion of IT technologies in most businesses. Technology is moving too fast, and threats even faster.
Our vulnerability management services will prioritize risks associated with your IT products & services based on their probability and urgency. If we discover a risk, we can work quickly alongside your people to fix or mitigate the issue with appropriate remediation measures.
SECURITY INFORMATION AND EVENT MANAGEMENT (SIEM)
Our experts will do this by leveraging your existing analytics (and content) wherever possible with relevant SaaS.
We also utilize User and Entity Behavior Analytics (UEBA) to discover security anomalies, including:
- Firewall rules management
- Security and software monitoring
- Incident response
- Threat intelligence
IDENTITY AND ACCESS MANAGEMENT (IAM)
Who can access your IT system? Where? When? How? Access is your first line of defence, and it must be carefully protected.
Agile IAM technologies combine administration, analytics, authorization and assurance to improve the experience for your customers and stakeholders as your organization moves towards digitalization.
We can incorporate IAM within your online operations, and include specialized features such as:
- Identity Analytics – to clean up user data and continuously evaluate risk
- Continuous Adaptive Trust and Risk Assessment (CARTA) – an agile way to manage access that does away with privileged access and password-only authentication
- Passwordless Authentication – using biometric recognition technologies
SECURITY OPERATIONS
Day-to-day detection and response to security threats depends on more than automated security tools alone. Cyber security can only be genuinely effective when carried out methodically by skilled professionals.
Engaging dig8ital to manage your security operations means you will have expert consultants on-hand, empowered by contemporary security tools, to detect and respond to threats so your organization can operate with stability, resilience and efficiency.
We will work alongside your people to gain a genuine understanding of your key business assets and drivers, just as we do ahead of any digital transformation and strategy project.
