CYBER SECURITY RISK
BALANCE RISK WITH A POSITIVE CUSTOMER EXPERIENCE
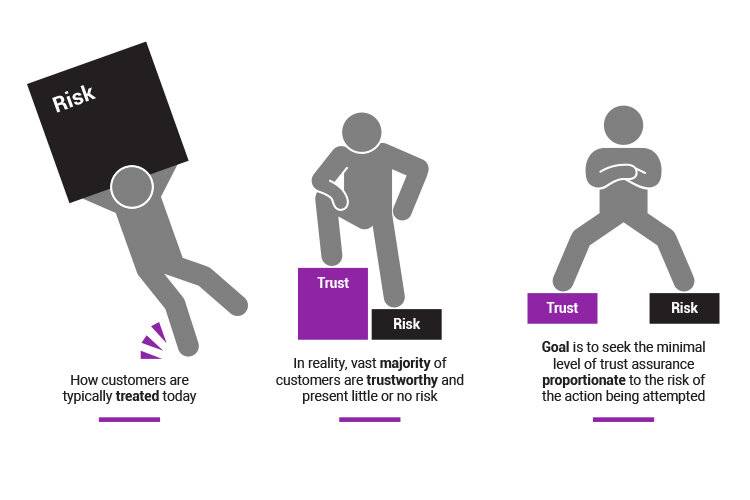
Many organizations have unnecessarily strong cyber security measures in place, treating customers like criminals and making the customer experience more difficult – less convenient.
But, the reality is that most customers present little risk to your business. Therefore, you must learn to balance maintaining security measures while still providing a convenient customer experience.
At dig8ital, we can help you create that balance by identifying your risk appetite, assessing and managing risks, and monitoring for, simulating and responding to breaches.
HOW DIG8ITAL CAN HELP
- Identify customer experience touchpoints in the security process, and evaluate the trust-risk balance
- Bring customer experience into security projects and products
- Develop metrics to report on customer experience within cyber security
- Test, evaluate and iterate cyber processes to ensure they are fit for purpose
- Demonstrate transparency to customers, helping earn their trust
- Develop new company policies on the topics of risk, security and communication with customers
DETERMINE YOUR RISK APPETITE
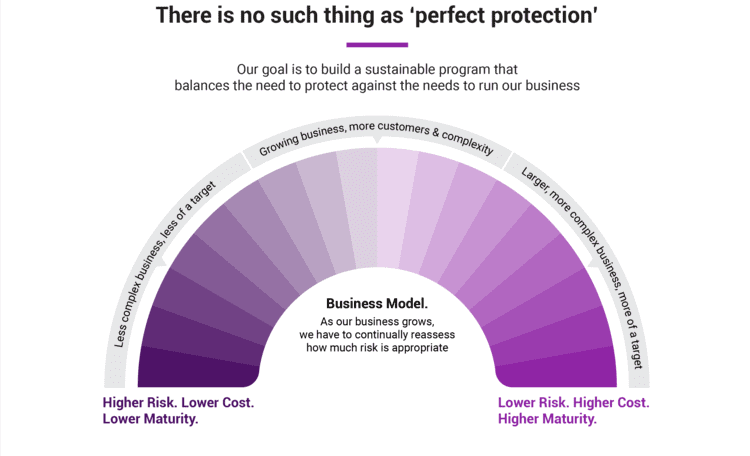
The use of cloud-based solutions in business is growing, yet many organizations fail to evolve their data security measures to suit this new way of working. So, identifying how your organization balances risk with current day-to-day operations is the first step to enhancing data protection.
Our security experts can guide you in changing outdated thinking and challenging assumptions so you can explore the most effective options for protecting your business now – and in the future.
We have the tools to support you in identifying your risk appetite, which can help you find a level of risk that you’re comfortable with, aligned to your business goals and desired customer experience.
At dig8ital, we can help develop data security governance measures in line with your stated risk appetite and shareholder expectations, as well as assist in identifying potential threats – and how to mitigate them.
In addition, we recognise that threats can also come from within – even if only accidentally. We can work with your leaders to build a top-to-bottom cyber-safe company culture that prioritises education and minimises potentially costly accidents.
FINANCIAL DATA RISK ASSESSMENT
Your data is one of your most sensitive assets, but the importance of data differs from department to department – for some, it will be a worthwhile competitive advantage, whereas for others the risk could outbalance the benefit.
Assessing the risk of your organization’s data assets from department to department will help your leaders prioritize investment so those who need it, have it, whereas those who would find it too risky are restricted in their access.
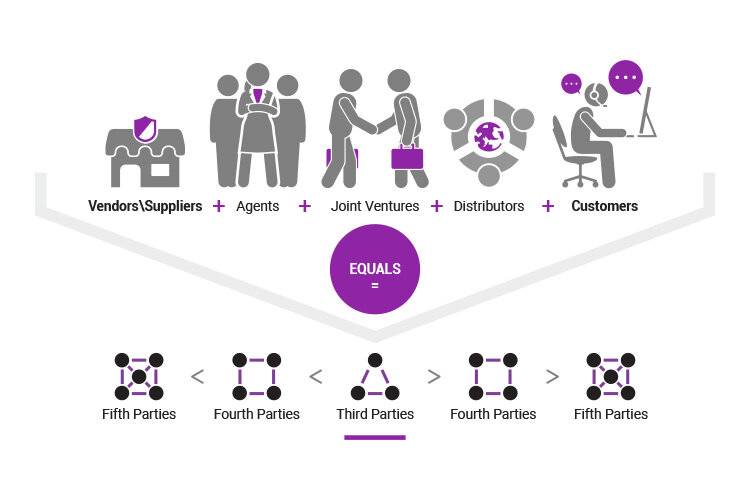
THIRD PARTY AND VENDOR RISK MANAGEMENT
In the modern global digital supply chain, your company is only as secure as its partners.
Forming partnerships with third parties and vendors goes hand in hand with digital transformation. But, any security weakness at the other end of these relationships could pose a threat to your business – and a back door for attackers.
So, we work with organizations to establish self-improving business processes that rank, assess and respond to risks presented by vendors.
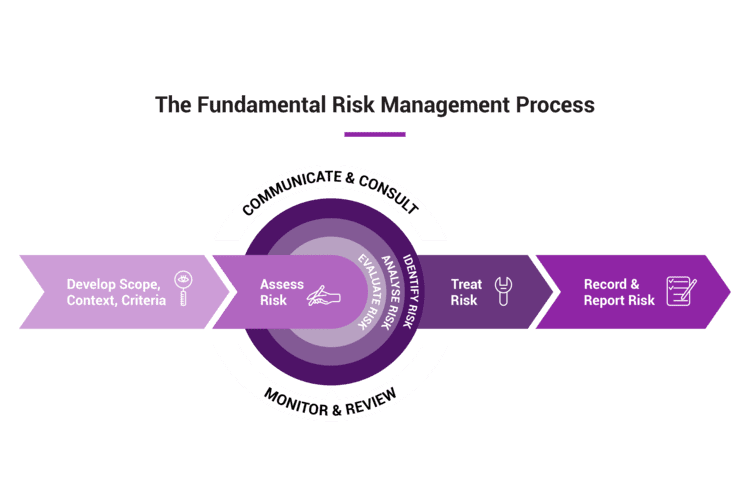
INTEGRATED RISK MANAGEMENT
No matter where you are on your digital transformation journey, a risk management process that hinges on legacy governance and compliance-directed approaches will make you vulnerable.
On the other hand, Integrated Risk Management (IRM) processes can support your business as you establish new products, services, skills and operations in the digital economy.
IRM is a flexible architecture that marries your business with technology. Our specialty in this area will help you build resilience across your organization so you can assess and treat risks efficiently and effectively, no matter where or when they arise.
BREACH DETECTION AND RESPONSE
Regular assessments of your cyber resilience will strengthen your organization’s ability to respond to attacks. Through each dig8ital assessment, we will give you the latest tools, processes and methodologies necessary to respond to up-to-the minute digital threats.
DETECTION
Security monitoring is often overscoped in the name of robust protection. However, more tools can actually increase security concerns by burdening security operations.
At dig8ital, we can ensure your detection methodologies complement the risks identified as important to your business. This means detection functions won’t overlap, and their use will be as simple as possible.
- Signatures
- Rules
- Correlation
- Analytical
- Deceptive
BREACH AND ATTACK SIMULATION
Short of facing a real attack, the only way to gain genuine insight into the strength of your security parameters is to put them to the test.
Our experts will simulate a series of attacks designed to infiltrate various levels of your digital network, exposing and assessing any security weaknesses – before an attacker does the same.
Our simulated attack strategies include:
- Physical infiltration
- Low-visibility reconnaissance
- Insider-assisted
- True outsider
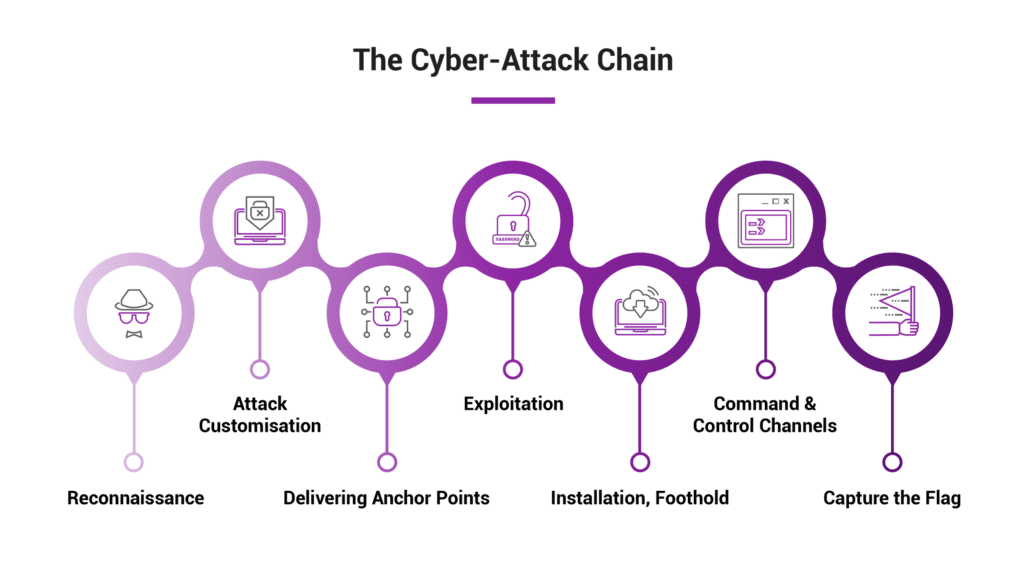
- Cyber kill-chain style
