PRIVACY MANAGEMENT & DATA PROTECTION
MINIMIZE THE RISK TO YOU AND YOUR CUSTOMERS WITH A STEP-BY-STEP PRIVACY PROGRAM
Data privacy is more than just a matter of regulatory compliance. Brand name, reputation, consumer trust, share price, these are all intrinsically linked with the concept of data protection.
For this reason, companies cannot afford not to have a clearly defined, structured approach to protecting their data. Just one breach could undo years of your hard work.
That’s where we come in. At dig8ital, we can help you develop a tailored privacy program that meets the needs of your business goals, matches your company culture and fits with the requirements of your wider industry sector.
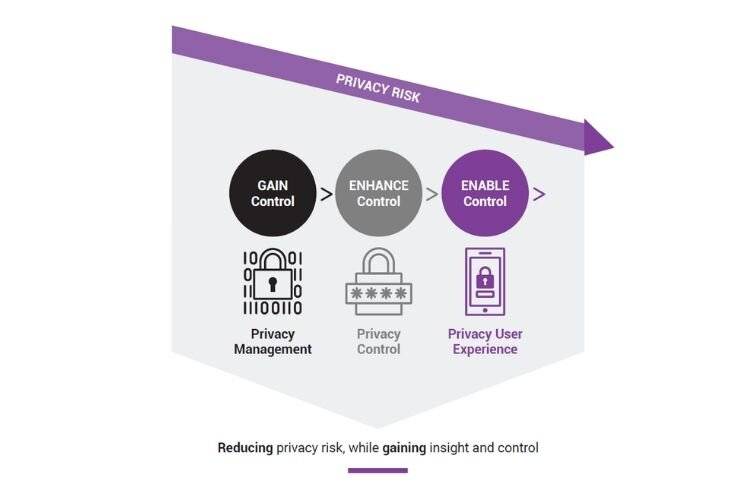
STARTING WITH GOOD PRIVACY GOVERNANCE
‘Privacy governance’ refers to the components which guide an organization’s privacy function towards regulatory compliance, in support of its broader business mission and goals. Get this part right, and the rest should fall into place.
But what are these components? Some examples include:
- Defining the vision and mission statement
- Defining the scope of the privacy program
- Selecting an appropriate privacy framework
- Developing the organizational privacy strategy
- Structuring the privacy team
You cannot protect what you don’t know is there. Any privacy program will struggle to succeed without your company first gaining a comprehensive view of its data assets and processes. Are you giving notice? Asking for consent? Offering choice? Limiting your retained data? Gathering data for an acceptable purpose?
A thorough data assessment can help you to inventory and track personal information in your company, as well as determine the impact your systems and processes will have on privacy.
Through this process, you will identify privacy risks in advance, so you can deal with them now – instead of waiting for them to become a major problem.
DATA ASSESSMENTS

PRIVACY BY DESIGN
Privacy by design anticipates and prevents breaches of trust before they happen – building privacy management into your systems and processes as their default. This makes privacy an integral component of your organization, and a key part of every product development stage.
This approach works because it takes into account the complete lifecycle of data in your business and combines each stage with strong security measures. At the same time you’re establishing visibility and transparency, helping you maintain accountability – and trust.

Responding to a data breach is highly complex, where every minute counts. Building a personal data incident response plan is, therefore, absolutely critical to the success of not just your privacy program management, but potentially your entire organization.
By building a fit-for-purpose incident response plan for a data breach, you’re building a process that clearly outlines who needs to do what, when, in the event of an attack. This will help you navigate the tricky legal waters surrounding cyber breaches, in addition to the post-notice scrutiny from regulators as well as the potential fallout among stakeholders.
HANDLING DATA BREACHES
STARTING WITH GOOD PRIVACY GOVERNANCE
We’re here to tailor a specific solution for your needs, not to force you into an out-of-the-box product. Our experts will sit down with your teams, understand your unique needs, and figure out how best to integrate privacy into the ways you already work – while encouraging you to evolve at the same time.
To enable success, our advisors will:
- Understand your current data landscape through data inventory assessments.
- Define a privacy management program based on your needs, and your legal requirements.
- Conduct data assessments and awareness sessions to make sure all personal information is properly protected.
- Establish a data breach incident response plan.
- Define a privacy policy.
- Define and implement a data classification policy.
- Conduct assessments on third parties.
- Establish privacy clauses for third-party contracts.
Tools our advisors use include:
- Data discovery
- Privacy impact assessments
- Vendors assessments
- Data loss prevention
- Data classification
- Data mapping
- Incident response planning
- Website scanning/cookie compliance
- Activity monitoring
- De-identification and pseudonymization
- GRC tools
