Recently, dig8ital tackled a significant cybersecurity challenge. Our goal? Conducting a thorough security assessment of a development pipeline for a company boasting over 50 active projects. For this endeavor, we leaned on the fresh insights from the OWASP Top 10 CI/CD Security Risks framework. This article unfolds our methodical approach, showcasing the depth and precision of our assessment process.
Context and scope of the assessment
dig8ital embarked on a mission with a prominent company known for its impressive portfolio of over 50 active projects. This company, while technologically advanced, recognized the imperative need for bolstering the security of their development pipeline. Most of their development teams operated within Azure, a testament to their commitment to cloud-first solutions. Notably, when it came to security, their teams predominantly relied on Azure DevSecOps. This platform not only streamlined their operations but also provided an integrated environment for development and security. The choice to use the newly unveiled OWASP Top 10 CI/CD Security Risks framework for the assessment stemmed from its comprehensive coverage of potential risks in CI/CD pipelines.
For a comprehensive understanding of the tools, practices, and benefits of DevSecOps within the Azure environment, delve into the official Azure DevSecOps page available at Azure’s official website.
Understanding the OWASP Top 10 CI/CD Security Risks Framework
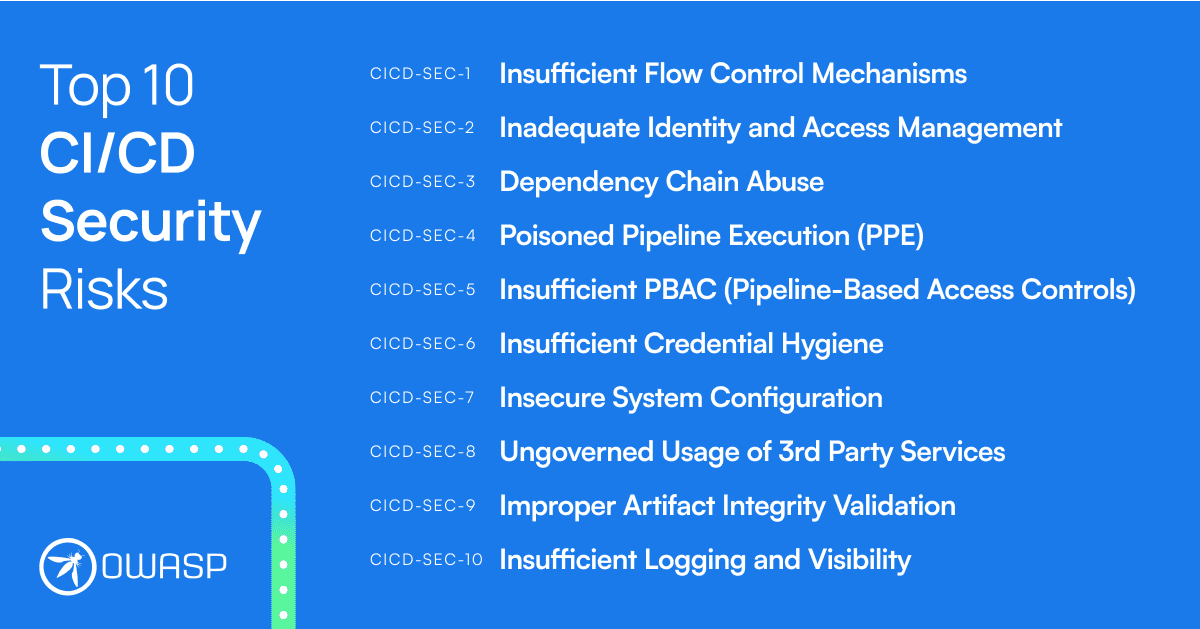
The OWASP Top 10 CI/CD Security Risks framework stands as a beacon for cybersecurity professionals. Developed by OWASP, a renowned entity in the cybersecurity realm, this framework pinpoints the most critical security risks in CI/CD pipelines. Let’s break it down:
- Insufficient Flow Control Mechanisms: Weak flow controls can allow attackers with system access in the CI/CD process to push malicious code without additional approval. Essentially, weak controls might let attackers skip code reviews and directly deploy harmful code.
- Inadequate Identity and Access Management: Weak identity and access management in the CI/CD pipeline can lead to unauthorized access. For instance, poor access controls might let attackers modify the pipeline, introducing malicious code.
- Dependency Chain Abuse: Attackers might exploit insecure dependencies within the CI/CD pipeline. They could use known vulnerabilities in a dependency to compromise the pipeline.
- Poisoned Pipeline Execution (PPE): Attackers can maliciously alter the pipeline to run unauthorized tasks. They might use this to run harmful scripts, leading to data theft or system breaches.
- Insufficient PBAC (Pipeline-Based Access Controls): Weak PBAC can result in unauthorized CI/CD pipeline actions. Attackers might exploit this to access sensitive areas, causing data breaches or harmful code deployment.
- Insufficient Credential Hygiene: Poor credential management within the CI/CD pipeline poses risks. Hard-coded credentials or unprotected secret keys can grant attackers unauthorized access.
- Insecure System Configuration: Security flaws across the pipeline can provide easy targets for attackers. For example, they might exploit weak configurations to access the CI/CD infrastructure.
- Ungoverned Usage of 3rd Party Services: Using third-party services without control can introduce security risks. Insecure integrations, like with a code scanning tool, might reveal sensitive data.
- Improper Artifact Integrity Validation: Weak artifact integrity validation can lead to malicious artifact deployment. Lack of checks might allow attackers to swap genuine artifacts with malicious ones.
- Insufficient Logging and Visibility: Inadequate logging can delay incident detection. Poor logging might let an attacker operate within the CI/CD environment undetected.
For a deeper dive into the framework and its intricacies, consider exploring the official OWASP Top 10 CI/CD Security Risks documentation.
Methodology: Navigating the Assessment Process
Our assessment’s foundation lay in a collaborative approach. We believed that firsthand insights from those working within the system would be invaluable. Here’s how we proceeded:
- Stakeholder Interviews: Our journey began with in-depth interviews with the SecOps leaders. Their insights offered a macro perspective, laying the groundwork for our subsequent steps. We also engaged with other cybersecurity expert teams, ensuring a holistic understanding of the pipeline’s current security posture.
- Access and Deep-Dive Examinations: Post initial discussions, we requested access to dive deeper into specific areas of the CI/CD pipeline. This enabled us to conduct exhaustive examinations, identifying vulnerabilities that might otherwise go unnoticed.
- Automation in Assessment: In our bid to leave no stone unturned, we employed automation tools. Automated scans of repositories were conducted to identify potential code vulnerabilities. Additionally, we leveraged tools to detect misconfigurations, weak access controls, and unpatched dependencies. This not only improved the efficiency of our assessment but also ensured comprehensive coverage.
- Immediate Reporting: A core tenet of our methodology was agility in communication. Every finding, no matter how minor, was immediately reported to the respective team. This swift reporting mechanism allowed issues to be addressed promptly, minimizing potential risks.
The Comprehensive Report: Insights, Analysis, and Recommendations
At the culmination of our assessment, a detailed report was meticulously crafted to provide the company with actionable insights. Here’s a breakdown of its components:
- Executive Summary: This section was penned by our lead expert, offering a holistic view of the entire assessment. Beyond just listing out findings, the expert provided a strategic perspective, suggesting overarching improvements and innovative ideas to bolster the CI/CD pipeline’s security posture.
- Detailed Findings: For each identified vulnerability or issue, a thorough analysis was presented. We employed a dual metric of ‘Probability’ and ‘Impact’ to gauge the significance of each finding for the company. This approach ensured that the company had a clear understanding of the potential repercussions of each vulnerability.
- Key Recommendations: Our report didn’t just stop at identifying problems; it presented solutions. For every finding, a set of key recommendations was provided, tailor-made to address the specific challenges identified.
- Prioritized Roadmap: Recognizing the need for a structured approach to address the findings, we included a prioritized roadmap. This roadmap acted as a strategic guide, detailing the sequence in which the recommendations should be implemented. It was designed to give the company a clear path forward, ensuring that the most critical vulnerabilities were addressed first.
For an insightful read on the nuances between DevOps and DevSecOps, and a deeper understanding of the latter, refer to our last article here.
Final Thoughts
Our collaboration with the company underscores the critical importance of proactive cybersecurity measures in today’s digital landscape. The assessment, rooted in the OWASP Top 10 CI/CD Security Risks framework, illuminated areas of improvement and provided a clear path forward. Through detailed analyses, strategic recommendations, and a prioritized roadmap, we aimed to empower the company to fortify its CI/CD pipeline. The journey underscored a shared commitment to excellence and security, setting a benchmark for future endeavors.